How to Install a Private OpenVPN Server on Ubuntu 22.04

Amid the age of growing privacy concerns, we often look for options to browse the internet safely without relying on third-party services. Setting up a private VPN (Virtual Private Network) server is one of the secure solutions in these times. OpenVPN offers one of the most trusted and flexible VPN solutions, which allows you to set up a private network that shields your data from potential network vulnerabilities. Some popular use cases of using a VPN include but are not limited to, bypassing regional restrictions, securing usage of public Wi-fi, and so on.

In this guide, we'll walk you through a step-by-step approach to setting up your own OpenVPN server on Ubuntu 22.04. We recommend thoroughly following this guide from installation to starting the server so you can seamlessly set up the server without errors!
Prerequisites
- A Virtual Machine (such as the ones provided by NodeShift) with:
- 2 vCPUs
- 2 GB RAM
- 10 GB SSD
- Ubuntu 22.04 VM
Note: The above prerequisites are highly variable across use cases. A high-end configuration should be used for a large-scale deployment.
Step-by-step process to install private OpenVPN server on Ubuntu 22.04
For the purpose of this tutorial, we'll be using a CPU-powered Virtual Machine by NodeShift since it provides Compute Virtual Machines at a very affordable cost on a scale that meets GDPR, SOC2, and ISO27001 requirements. Also, it offers an intuitive and user friendly interface, making it easier even for beginners to get started with Cloud deployments. However, feel free to use any cloud provider of your choice, and follow the same steps for the rest of the tutorial.
Step 1: Setting up a NodeShift Account
Visit app.nodeshift.com and create an account by filling in basic details, or continue signing up with your Google/GitHub account.
If you already have an account, login straight to your dashboard.
Step 2: Create a Compute Node (CPU Virtual Machine)
After accessing your account, you should see a dashboard (see image), here:
- Navigate to the menu on the left side.
- Click on the Compute Nodes option.
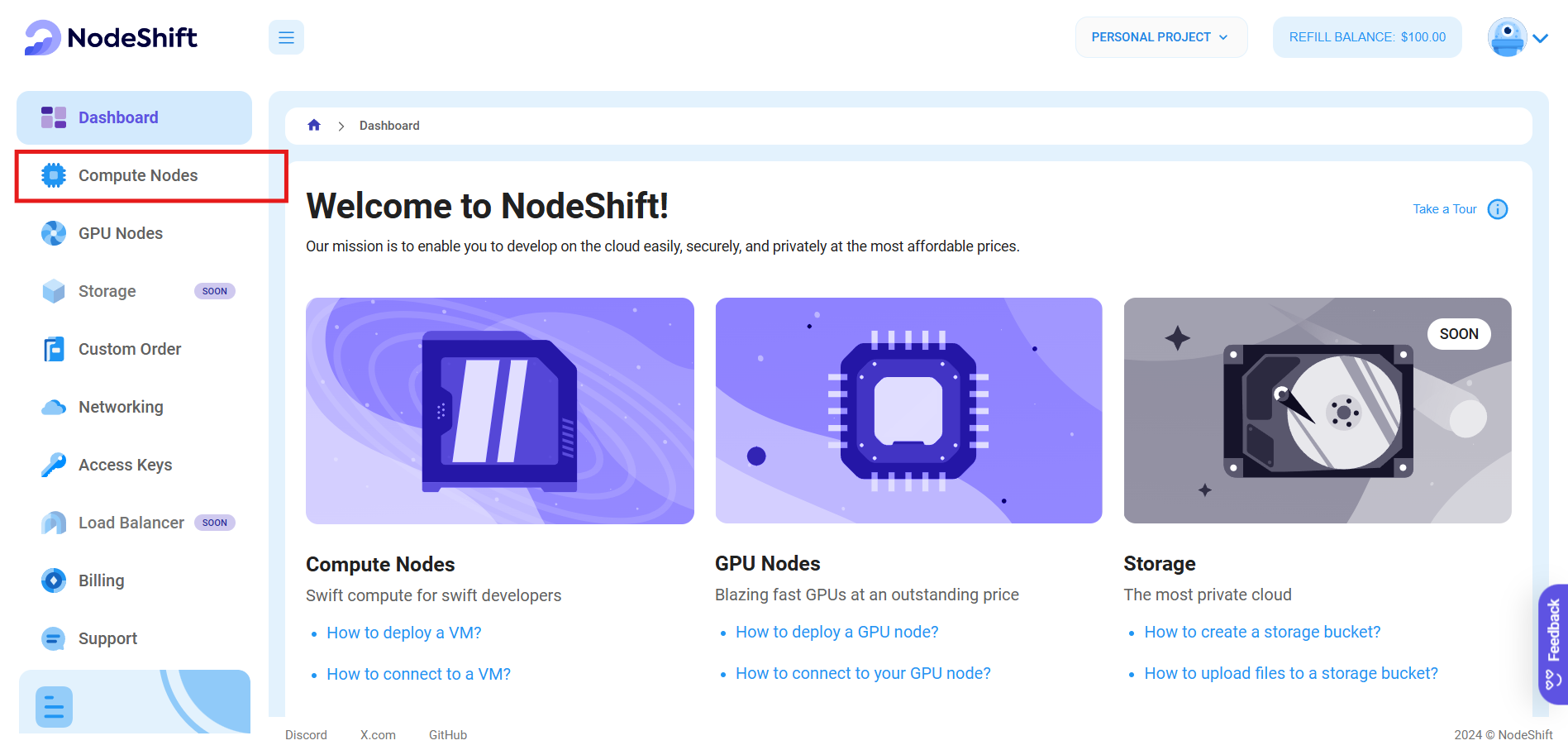
- Click on Start to start creating your very first compute node.

These Compute nodes are CPU powered virtual machines by NodeShift. These nodes are highly customizable, and let you control different environmental configurations, such as CPUs, RAM and storage, according to your needs.
Step 3: Select configuration for VM
- The first option you see is the Reliability dropdown, which lets you choose the type of uptime guarantee level you're seeking for your VM (e.g., 99%).

- Next, select a geographical region from the Region dropdown, where you want to launch your VM (e.g. United States).
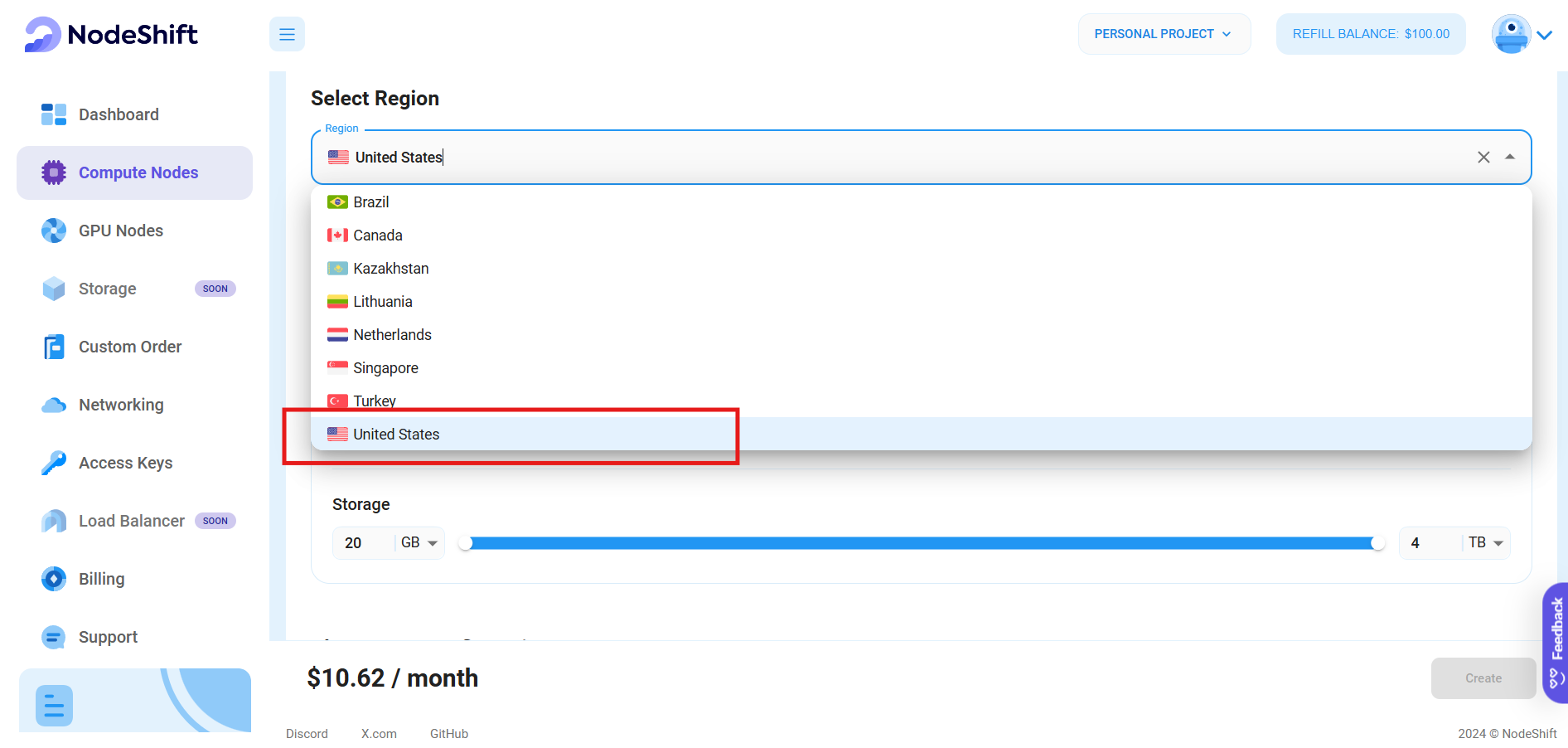
- Now, most importantly, select the right specifications for your VM according to your use-case by sliding the bars for each option.
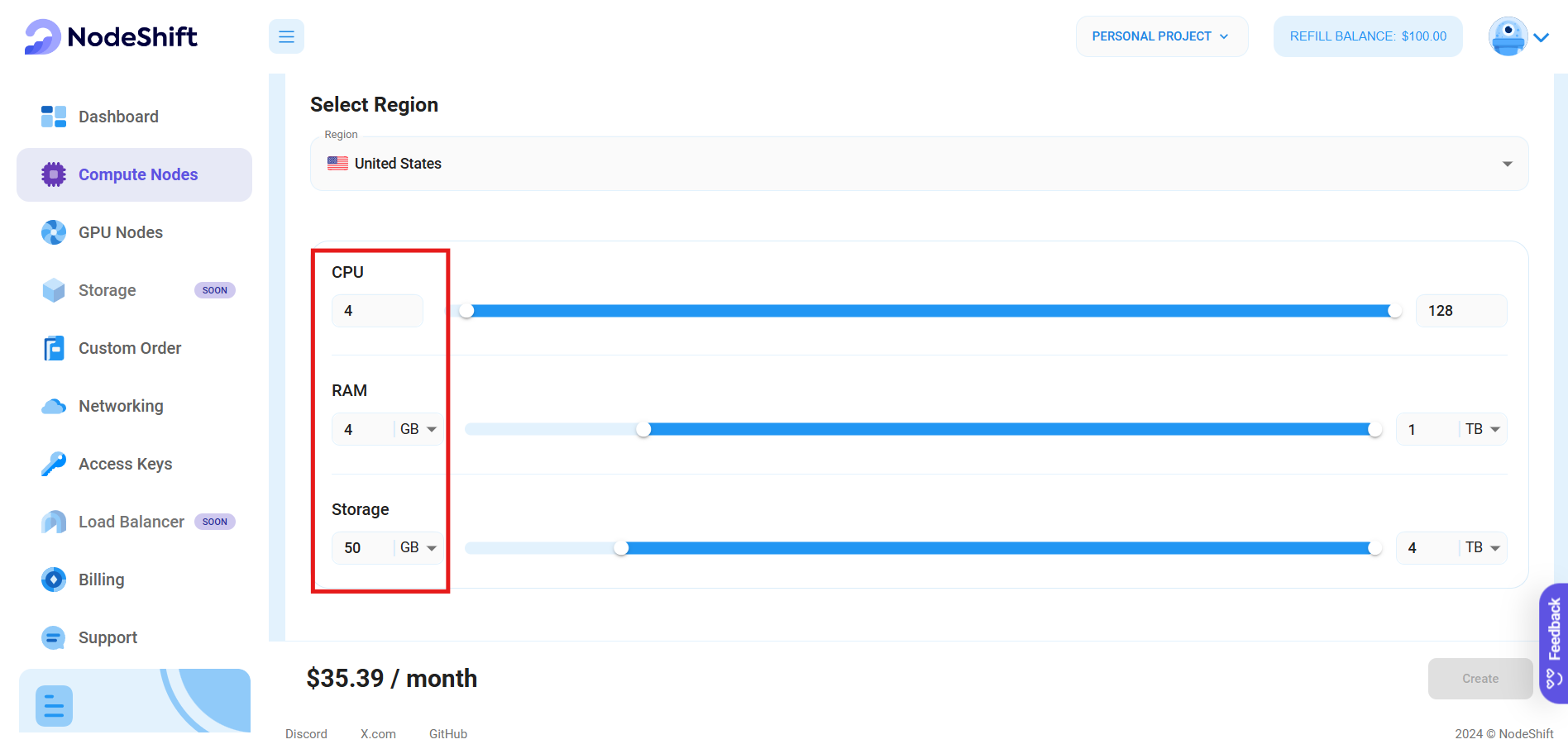
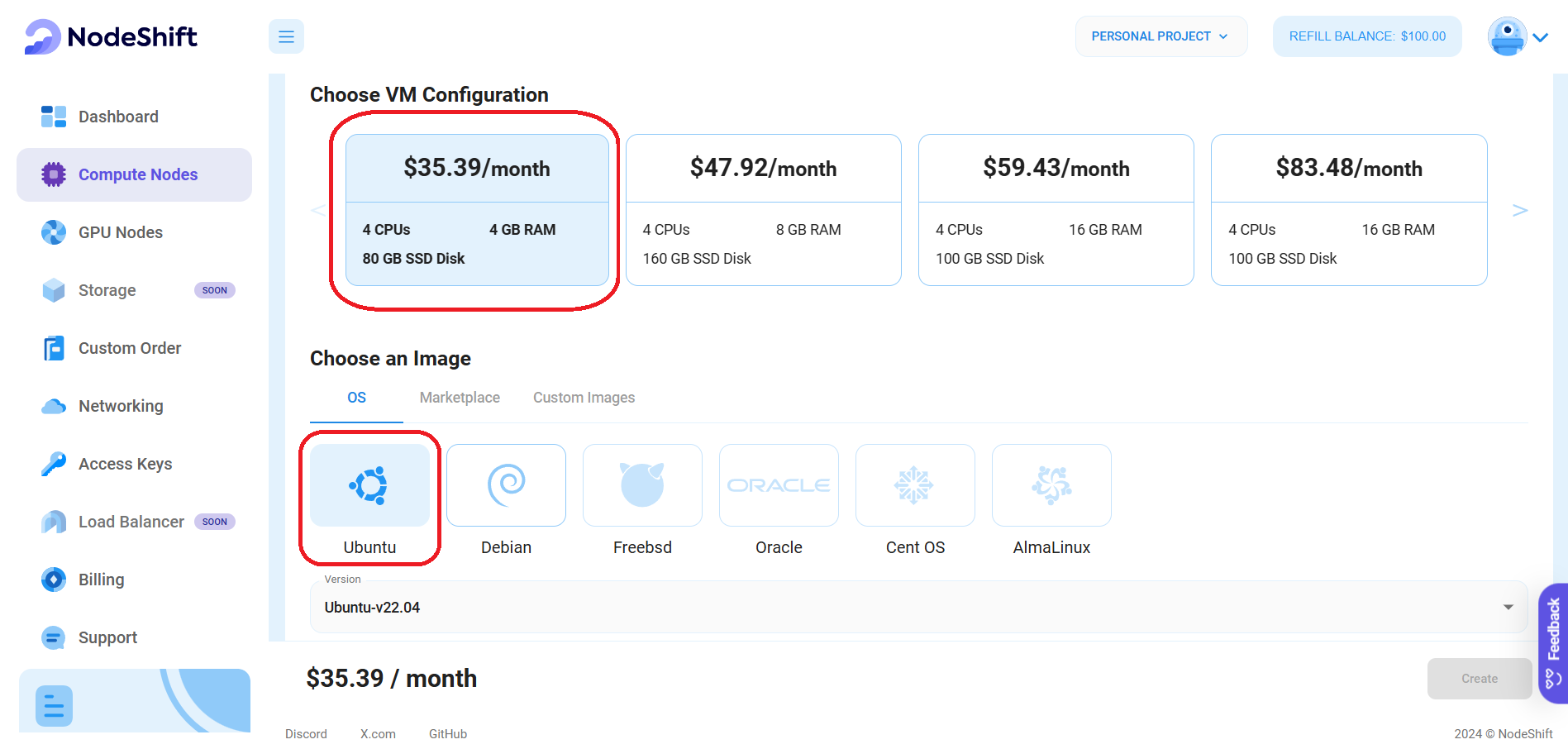
Step 4: Choose VM Configuration and Image
- After selecting your required configuration options, you'll see the available VMs in your region and as per (or very close to) your configuration. We'll be choosing a '4 vCPUs/4GB/80GB SSD' Compute node in our case.
- Next, you'll need to choose an image for your Virtual Machine. For the scope of this tutorial, we'll choose Ubuntu, but you can choose any other option where you want to set your VPN.
Step 5: Choose the Billing cycle and Authentication Method
- For the billing cycle, two options are available: Hourly being ideal for short-term usage, offering pay-as-you-go flexibility, and Monthly being best for long-term projects with consistent usage rate and potentially lower cost.
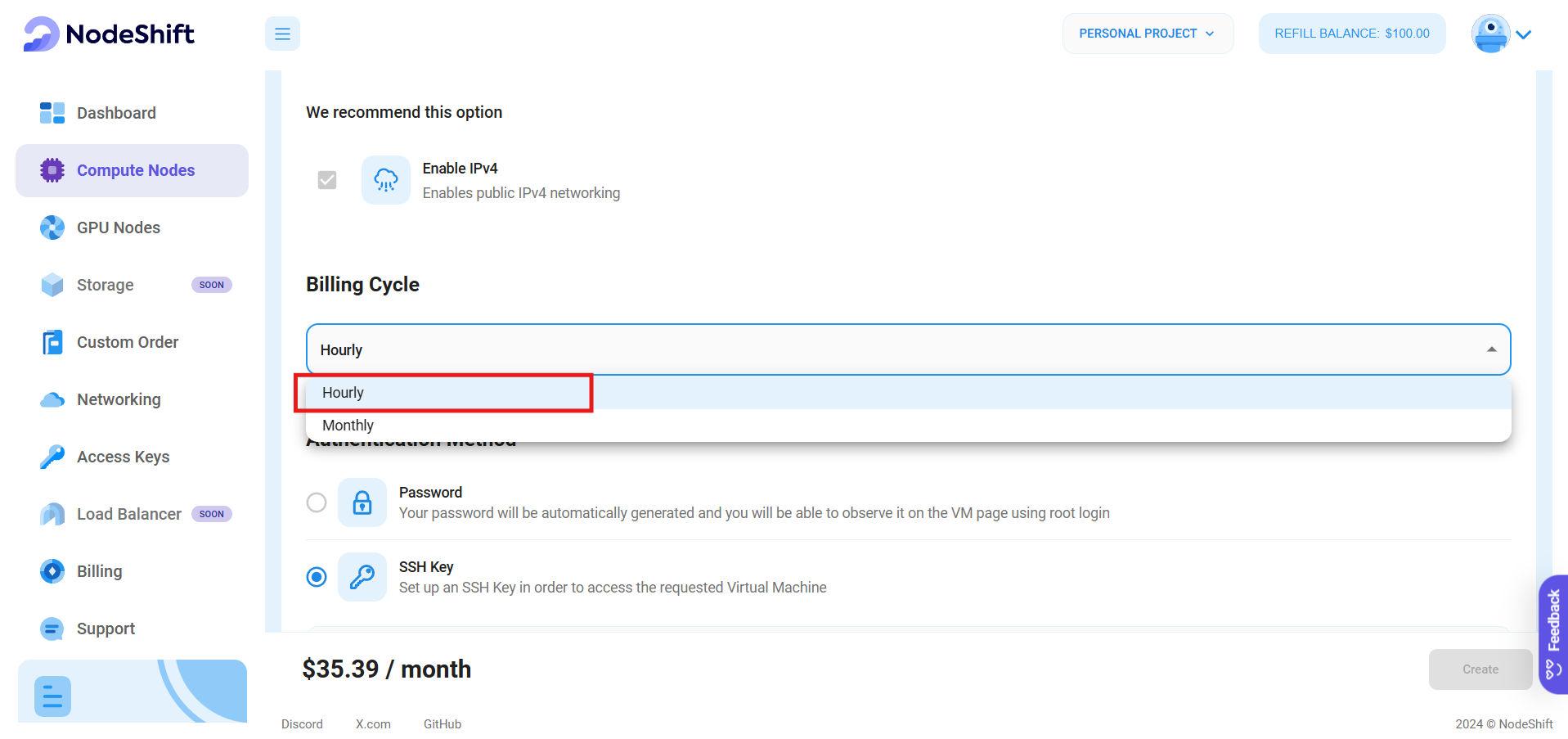
- Next, you'll need to select an authentication method. There are two methods available: Password and SSH Key. We recommend using SSH keys as they are more secure option. In order to create one, head over to our official documentation.

Step 6: Finalize Details and Create Deployment
Finally, if you may want, you can also add a VPC (Virtual Private Cloud), which provides an isolated section for you to launch your cloud resources (Virtual machine, storage, etc.) in a secure, private environment. We're keeping this option as default for now, but feel free to create a VPC as per your needs.
Also, you can deploy multiple nodes at once by clicking + in the Quantity tab.

That's it! Now, you are ready to deploy the node. Finalize the configuration summary, if it looks good, go ahead and click Create to deploy the node.

Step 7: Connect to active Compute Node using SSH
As soon as you create the node, it will take few seconds or a minute to get deployed, once it is deployed you will see a status "Running" in green meaning that our Compute node is ready to use!
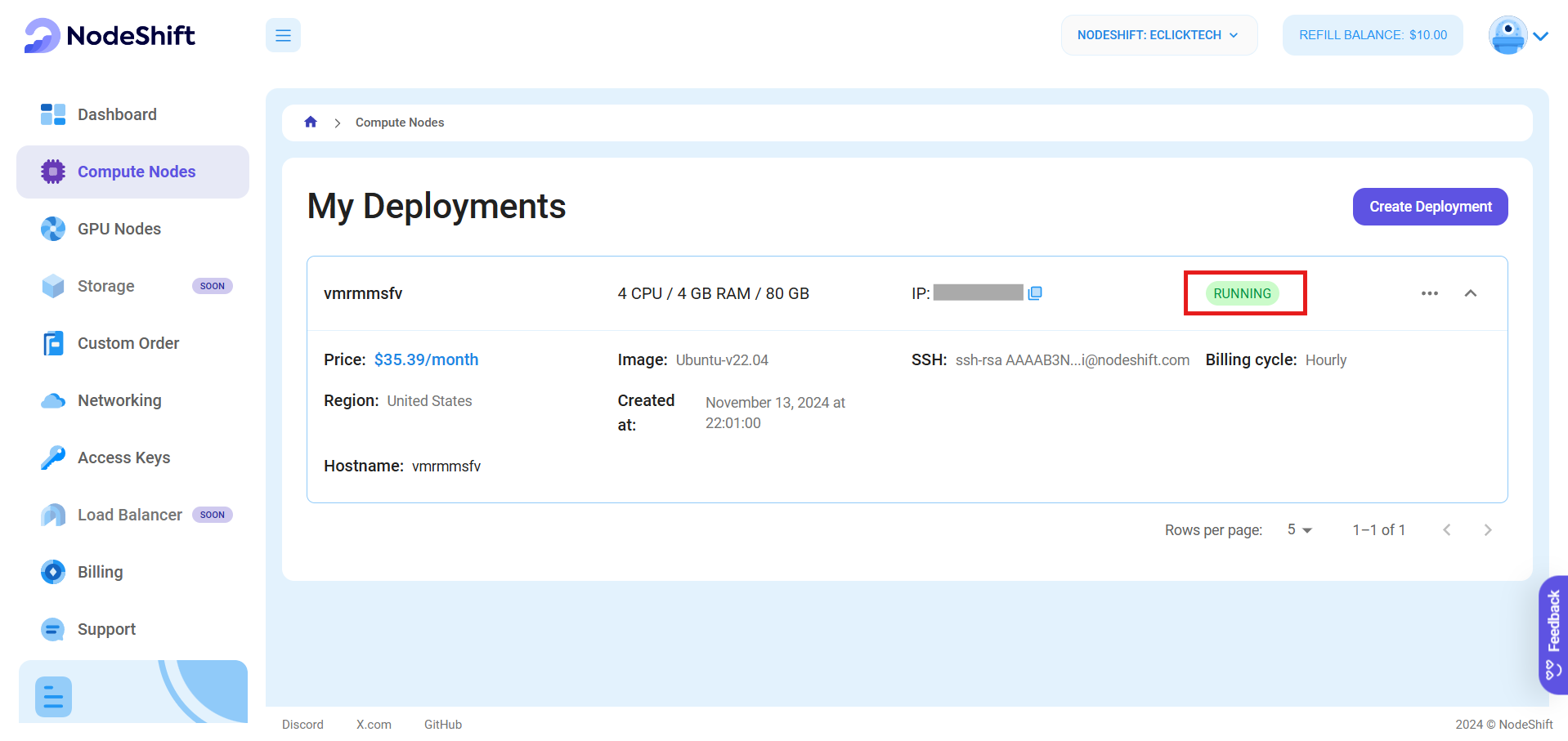
Once your node shows this status, follow the below steps to connect to the VM via SSH:
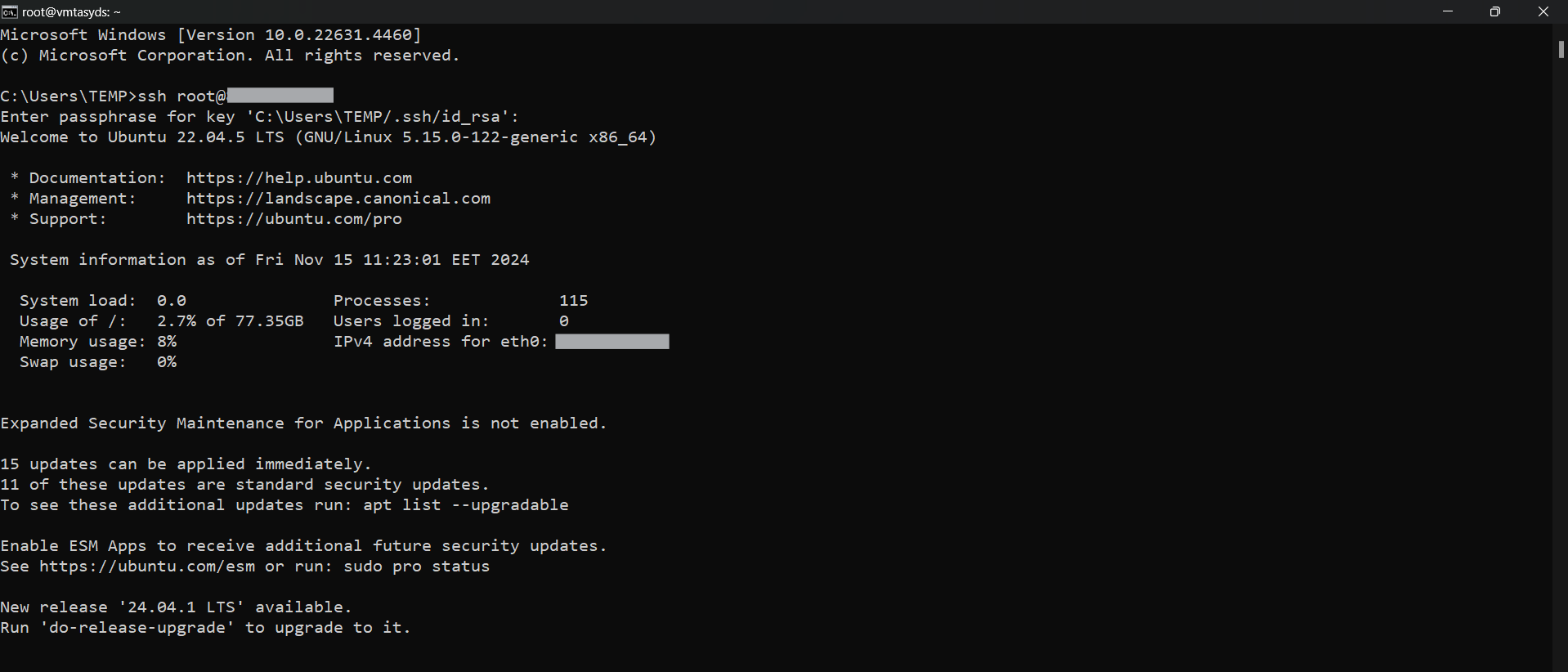
- Open your terminal and run the below SSH command:
(replace root with your username and paste the IP of your VM in place of ip after copying it from the NodeShift dashboard)
ssh root@ip
- If SSH keys are set up, the terminal will authenticate automatically.
- In some cases, your terminal may take your consent before connecting, enter 'yes', and you should be connected.
Step 8: Install Dependencies for OpenVPN
Before we move on to install OpenVPN, we first need to perform some prerequisites which are required for the installation of OpenVPN.
- Let's start by updating the Ubuntu package source list for the latest version and security updates
sudo apt updateOutput:

- Once the update is done, install OpenVPN.
sudo apt install openvpnOutput:

We'll need to install Easy-RSA along with OpenVPN, which serves as a utility for generating SSL certificates and keys for secure communication.
sudo apt install easy-rsaNote: In some cases, after executing the above command, you might come across an error like this:
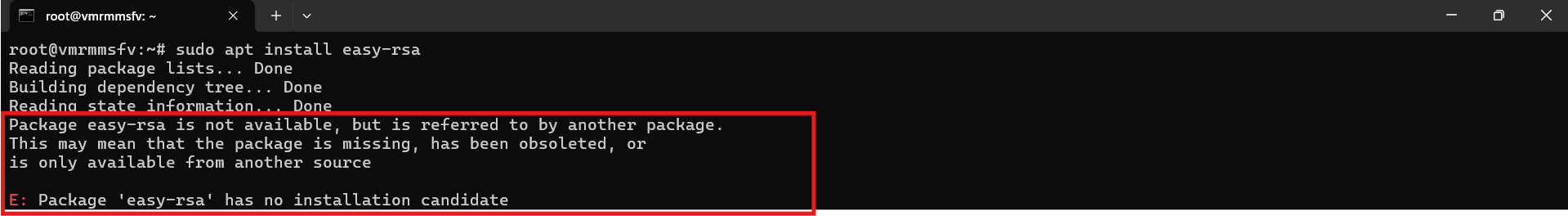
This usually occurs when universe repository, where easy-rsa is located, is not enabled.
Here's how to fix it:
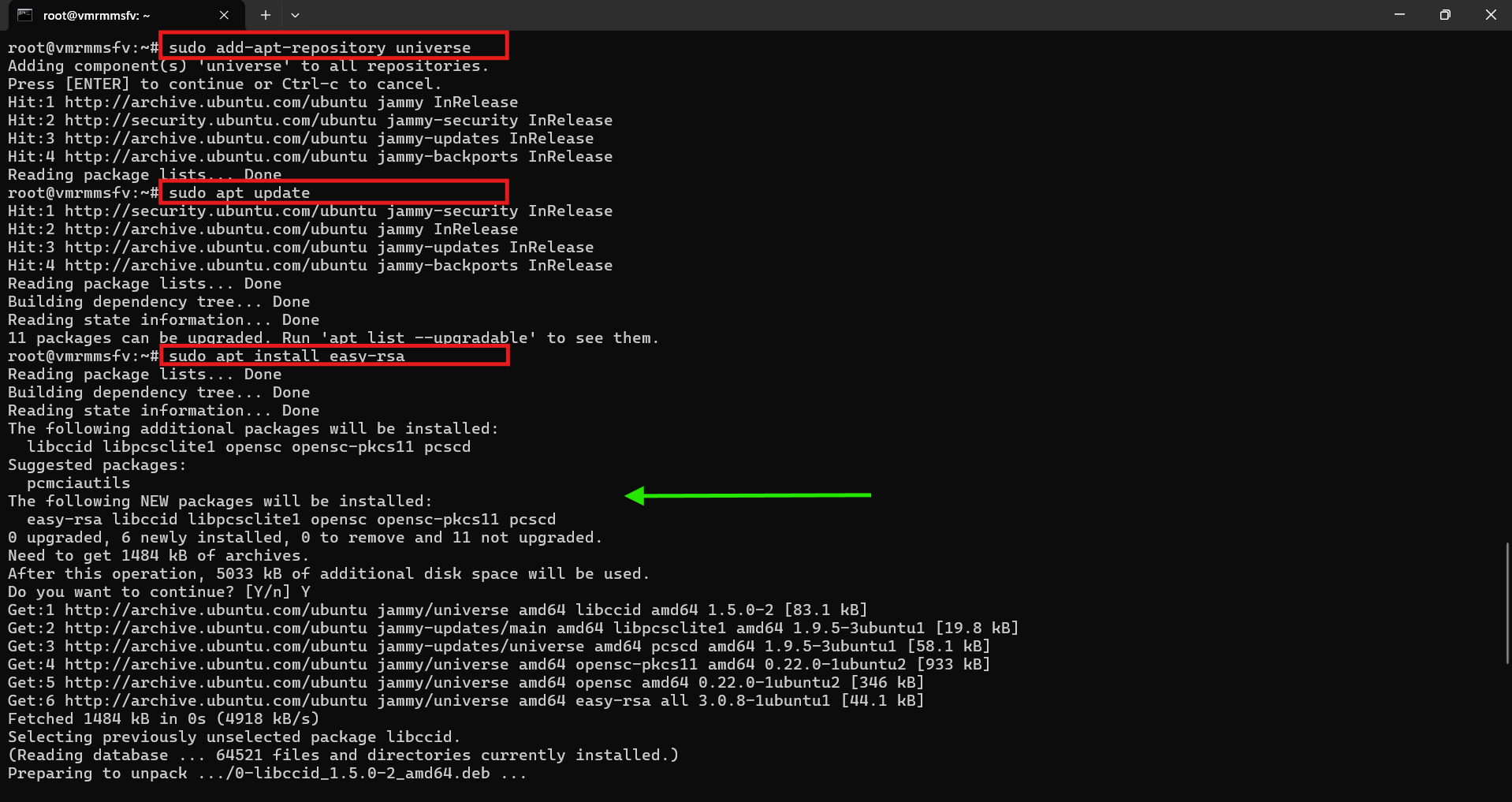
- Enable the universe repository
sudo add-apt-repository universe- Update the package source list again
sudo apt update- Once again, run the
easy-rsainstallation command, and now it should execute successfully.
Step 9: Initialize PKI (Public Key Infrastructure)
Once the above installation is done, proceed to set up PKI, which is essential for generating certificates and keys for OpenVPN.
To initialize PKI, you need to:
- Copy the Easy-RSA directory to an alternate location (as a safeguard measure)
sudo cp -r /usr/share/easy-rsa /etc/
- Navigate to the copied directory
cd /etc/easy-rsa/
- Initialize PKI
sudo ./easyrsa init-pki
Output:

Step 10: Generate Server Certificates and Keys
Next, we are ready to generate CA (certificate authority) and keys, follow the below steps thoroughly to successfully generate all the required certificates and keys for setting up OpenVPN server.
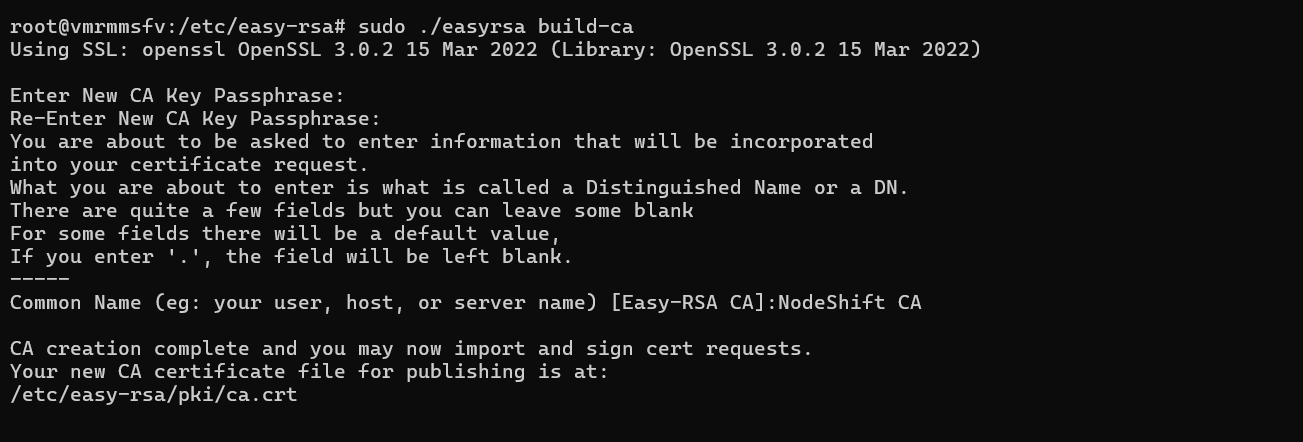
- Generate certificate authority
sudo ./easyrsa build-ca
Output:
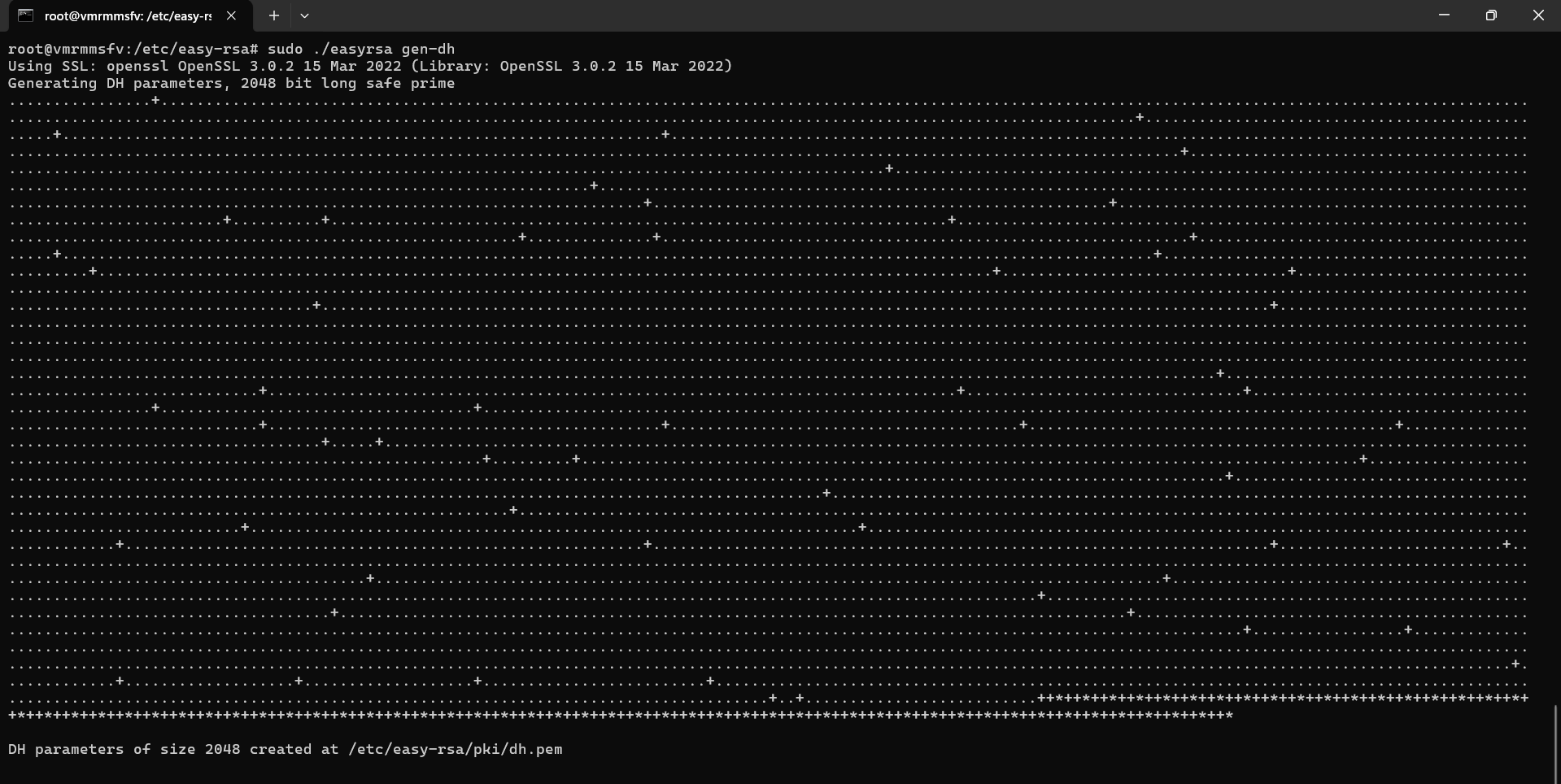
- Generate Diffie-Hellman parameters
sudo ./easyrsa gen-dh
Output:
- Generate OpenVPN server certificate and key
sudo ./easyrsa build-server-full server nopass
Output:
- Generate HMAC key
HMAC keys authenticate the integrity of data and packets, ensuring they come from a trusted source and have not been tampered with.
sudo openvpn --genkey secret /etc/easy-rsa/pki/ta.key
- Generate OpenVPN Revocation Certificate
OpenVPN revocation certificate ensures that an unauthorized client cannot use a revoked certificate to connect to the server.
sudo ./easyrsa gen-crl
Output:
- Copy server certificates and keys
Finally, we'll copy all the generated server certificates and keys to the server's configuration directory, which will be used to establish a secure connection between the server and client.
sudo cp -rp /etc/easy-rsa/pki/{ca.crt,dh.pem,ta.key,crl.pem,issued,private} /etc/openvpn/server/
Step 11: Generate Client Certificates and Keys
In this step, we'll generate unique certificates and keys for each client that needs to connect with our server.
- Create certificates and keys for a client
(replace clientname with the actual name of the client)
sudo ./easyrsa build-client-full clientname nopass
Output:
- Create directories for each client
sudo mkdir /etc/openvpn/client/clientname
- Copy the client files to its unique directory
sudo cp -rp /etc/easy-rsa/pki/{ca.crt,issued/clientname.crt,private/clientname.key} /etc/openvpn/client/clientname/
Step 12: Configure the OpenVPN server
- Copy a sample configuration file to OpenVPN server configuration directory. We'll edit these configuration as per our needs in next step.
sudo cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf /etc/openvpn/server/
- Edit the server configuration file.
sudo nano /etc/openvpn/server/server.conf
The above command will open the configuration file in Nano, which is a text editor, that will look something like this:
Go ahead and overwrite this file with the below configuration details (right-click on the editor to paste the below text)
port 1194
proto udp4
dev tun
ca ca.crt
cert issued/server.crt
key private/server.key # This file should be kept secret
dh dh.pem
topology subnet
server 172.16.20.0 255.255.255.0
ifconfig-pool-persist /var/log/openvpn/ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 208.67.222.222"
push "dhcp-option DNS 208.67.220.220"
client-to-client
keepalive 10 120
tls-auth ta.key 0 # This file is secret
cipher AES-256-CBC
persist-key
persist-tun
status /var/log/openvpn/openvpn-status.log
log-append /var/log/openvpn/openvpn.log
verb 3
explicit-exit-notify 1
auth SHA512The edited file should look something like this:
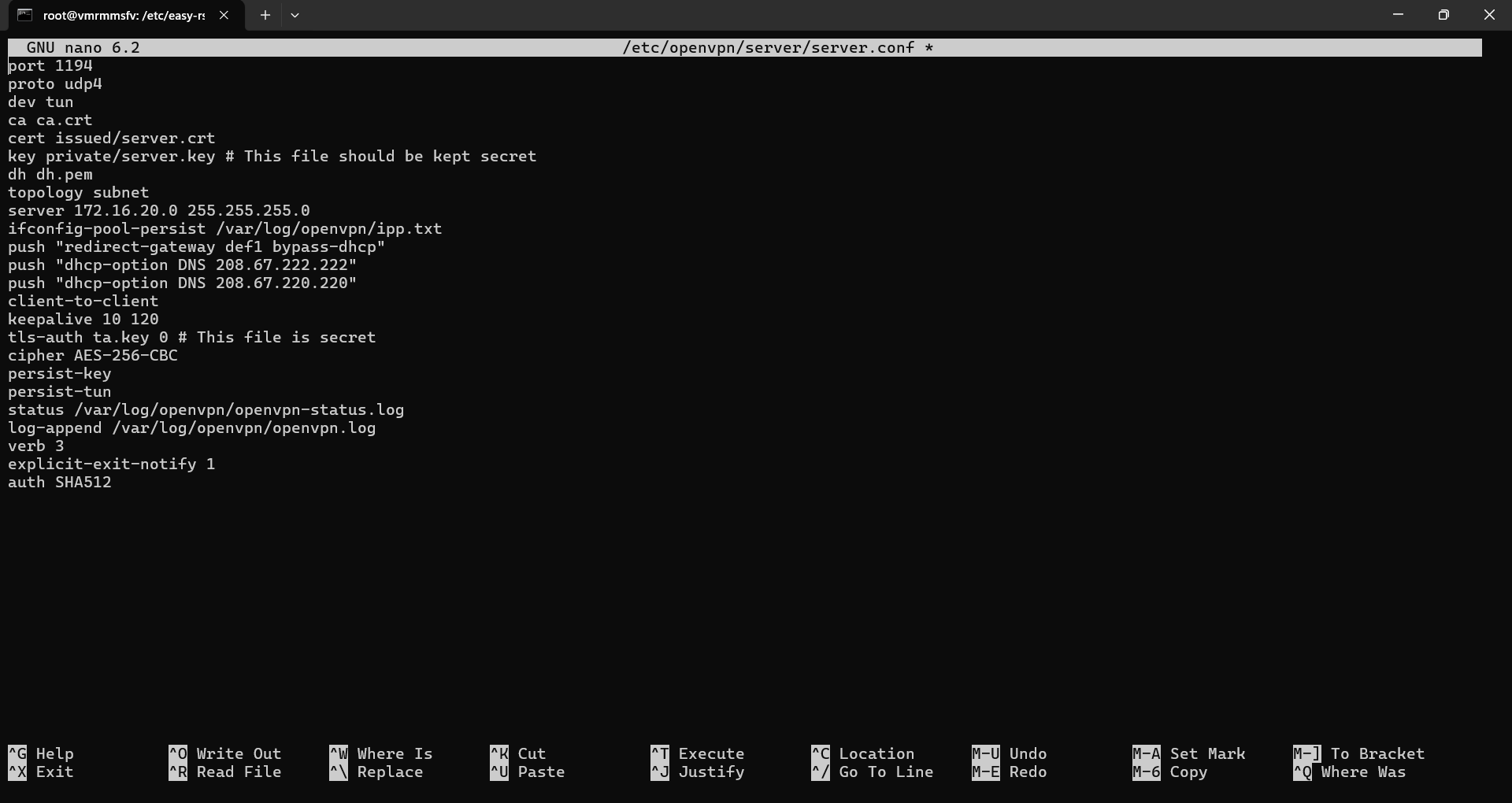
Save this edited file (Ctrl + O > Enter) and exit the editor (Ctrl + X).
This server configuration will set up an OpenVPN server on port 1194 using UDP along with other important specifications and network settings. Our server is now ready to route all client traffic through VPN, ensuring secure communication.
Step 13: Enable IP forwarding
IP forwarding will further help our server to route traffic between our client and other internal networks. This is crucial to allow client to access resources beyond a VPN server, such as public websites, remote server, etc.
- Enable IP forwarding
sudo sed -i 's/#net.ipv4.ip_forward=1/net.ipv4.ip_forward=1/' /etc/sysctl.conf
- Apply the changes to the server (without reboot)
sudo sysctl --system
Output:

- Configure firewall to allow traffic on UDP port 1194
sudo ufw allow 1194/udp
Output:

Step 14: Configure IP masquerading
IP masquerading is the technique that actually makes VPNs so powerful. It hides the individual client's IP behind its one main public IP so that any external website can only see the VPN server's public IP and not the client one.
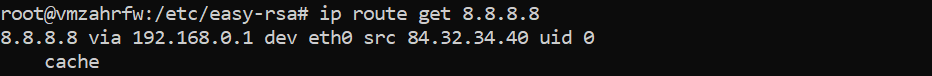
- Use the below command to identify the default network interface
ip route get 8.8.8.8
Output:
- Update UFW (Uncomplicated Firewall) rules
UFW is a user-friendly interface for managing firewalls in Linux-based systems.
Update the UFW configuration with the below command
sudo sed -i 's/DEFAULT_FORWARD_POLICY="DROP"/DEFAULT_FORWARD_POLICY="ACCEPT"/' /etc/default/ufw
- Reload UFW for changes to take effect
sudo ufw reload
Note: In some cases, after executing the above command, you might encounter an error like this:

to fix this, we'll need to enable the firewall:
sudo sed -ie 's/ENABLED=no/ENABLED=yes/' /etc/ufw/ufw.confafter this, go ahead to try the previous reload command again, and it should work fine this time.
Output:
Step 15: Start the OpenVPN Server
Finally, our server is ready to start and work. Let's run the final commands to start the server and see the logs.
- Enable and start the OpenVPN server
sudo systemctl enable --now openvpn-server@server
Output:

If you see the above output, it means our server has been started successfully.
- Check the log messages
sudo systemctl status openvpn-server@server
Output:
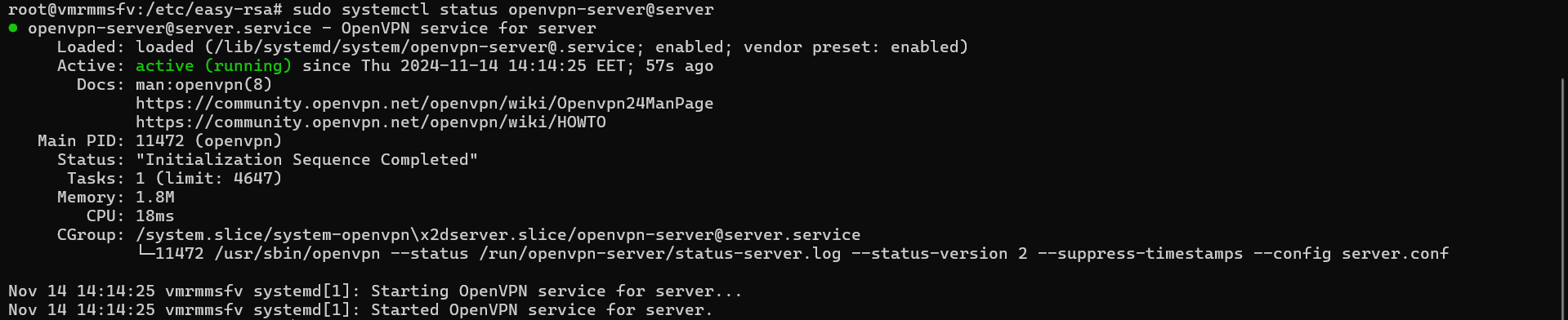
Congratulations, our OpenVPN private server is successfully up and running!
Conclusion
Setting up a private OpenVPN server on Ubuntu 22.04 provides a secure and safe way to access resources on the internet while maintaining privacy at the same time. This article approached this use case by deploying Ubuntu Virtual Machine on NodeShift-powered Compute Nodes. With NodeShift, you can leverage advanced computing capabilities, ensuring optimal efficiency and power for running VPNs without breaking the bank. Whether you're setting up a private VPN or deploying network services, NodeShift's streamlined cloud deployment offers a robust foundation for running secure and reliable server configurations seamlessly.
For more information about NodeShift:




